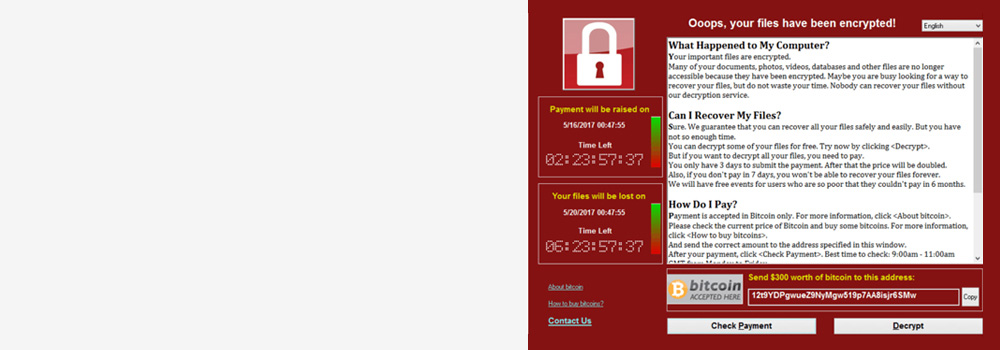
Professional Server Ransomware Data Recovery Services in Glasgow:
Ransomware attacks are one of the most devastating cybersecurity threats, especially for servers hosting critical business data. These attacks can result in encrypted data, operational downtime, and significant financial losses. Our Ransomware Professional data recovery services in Glasgow offer the expertise needed to recover encrypted files and restore business operations without compromising data security.
Understanding Ransomware Attacks
What is Ransomware?
Ransomware is malicious software designed to block access to data or systems by encrypting files, demanding a ransom payment in exchange for decryption keys.
Types of Ransomware
- Encryption Ransomware: Encrypts files and requires decryption keys.
- Locker Ransomware: Locks users out of the system but doesn’t encrypt files.
Common Methods of Attack
- Phishing emails with malicious attachments.
- Exploiting vulnerabilities in outdated software.
- Infiltrating weakly protected networks.
Symptoms of Ransomware Attack
- Files renamed or appended with strange extensions.
- Ransom notes appearing in file directories.
- Inaccessible files and applications.
Steps to Take After a Ransomware Attack
- Isolate Infected Systems
- Disconnect affected servers from the network to prevent the spread of ransomware.
- Avoid Paying the Ransom
- Paying does not guarantee data recovery and may encourage further attacks.
- Consult Professional Services
- Engage experienced ransomware recovery providers to assess and mitigate the attack.
- Secure Backups
- Verify the integrity of backups before initiating restoration efforts.
Professional Ransomware Data Recovery Services in Glasgow
Key Features of Recovery Services
- Expertise in handling encryption-based ransomware.
- Use of advanced tools for decrypting data and rebuilding damaged file systems.
- Support for Windows, Linux, and other server environments.
Server Ransomware Recovery Process
- Initial Assessment
- Identifying the type of ransomware and extent of encryption.
- Isolating the Environment
- Ensuring the ransomware doesn’t spread further.
- Decryption and Recovery
- Using specialised tools to attempt decryption.
- Recovering data from unaffected backups or encrypted volumes.
- Restoration and Prevention
- Rebuilding systems and implementing robust cybersecurity measures.
FAQs About Server Ransomware Data Recovery Services
- Can all types of ransomware be recovered without paying the ransom?
While many ransomware types have known decryption tools, success depends on the specific variant and extent of encryption. - How long does ransomware recovery typically take?
Recovery times range from a few days to several weeks, depending on complexity and data volume. - Is it possible to recover data without backups?
Yes, partial recovery is often possible using advanced decryption and data extraction techniques. - What should I do if I discover a ransomware attack on my server?
Immediately isolate the server, avoid interacting with the ransomware, and contact our Ransomware professional recovery service. - How can I ensure my data is safe after recovery?
Implement robust cybersecurity measures, such as regular backups, patch management, and employee education. - Is server ransomware recovery expensive?
Recovery costs vary based on the complexity of the attack but are less expensive than paying a ransom.
Ransomware is a type of malicious software designed to block access to a computer system or its data, usually by encrypting files, until a ransom is paid. Below are the main types of ransomware categorised by their behaviour and method of operation:
1. Crypto Ransomware
- What it does: Encrypts files on the victim’s system, making them inaccessible without a decryption key.
- Goal: To force the victim to pay for the decryption key to regain access to their data.
- Example Variants:
- WannaCry: Spread globally in 2017, exploiting a Windows vulnerability.
- CryptoLocker: One of the earliest and most infamous examples of crypto ransomware.
2. Locker Ransomware
- What it does: Locks users out of their devices or systems without encrypting files. The operating system becomes inaccessible.
- Goal: To demand payment to unlock the device.
- Common Characteristics: Displays a lock screen with a ransom message.
- Example Variants:
- Reveton: Often disguised as a law enforcement notice demanding a fine.
3. Double Extortion Ransomware
- What it does: Encrypts data and exfiltrates sensitive files. The attacker threatens to leak or sell the data if the ransom is not paid.
- Goal: To pressure victims into paying not only for decryption but also for preventing a data leak.
- Example Variants:
- Maze: Known for pioneering this double extortion tactic.
4. Ransomware-as-a-Service (RaaS)
- What it does: A business model where ransomware developers sell or lease ransomware kits to affiliates who then carry out attacks.
- Goal: To lower the technical barrier for entry into ransomware attacks, enabling less experienced cybercriminals.
- Example Variants:
- DarkSide: Used in the Colonial Pipeline attack in 2021.
5. Scareware
- What it does: Displays fake warnings about viruses or system issues and demands payment to “fix” the problem.
- Goal: To exploit fear and trick users into paying for a solution.
- Characteristics: Usually doesn’t encrypt files but locks the system or displays persistent pop-ups.
- Example Variants:
- Fake antivirus or system optimization tools.
6. Fileless Ransomware
- What it does: Operates entirely in the computer’s memory, avoiding detection by traditional antivirus software.
- Goal: To encrypt or lock data without leaving a significant footprint on the disk.
- Example Variants:
- Sodinokibi (REvil): A notorious variant that uses fileless techniques.
7. Master Boot Record (MBR) Ransomware
- What it does: Attacks the master boot record (MBR) of the system, rendering it unbootable. Often used in conjunction with encryption.
- Goal: To make the system completely inoperable until a ransom is paid.
- Example Variants:
- Petya: Rewrites the MBR, preventing the system from booting.
8. Mobile Ransomware
- What it does: Targets mobile devices, locking the screen or encrypting files stored on the device.
- Goal: To exploit the growing dependence on mobile devices and demand payment for unlocking or restoring data.
- Example Variants:
- Congur: A mobile ransomware strain that locks devices.
9. Wiper Ransomware
- What it does: Appears to be ransomware but is designed to destroy data rather than encrypt it.
- Goal: To cause maximum damage, often used in politically motivated or revenge-based attacks.
- Example Variants:
- NotPetya: Masqueraded as ransomware but wiped data irreversibly.
10. IoT Ransomware
- What it does: Targets Internet of Things (IoT) devices, such as smart appliances, routers, or cameras.
- Goal: To exploit the lack of robust security measures in IoT devices and demand payment for restoring functionality.
- Example Variants:
- Hajime: A ransomware strain targeting IoT networks.
11. Ransomware Targeting Cloud Services
- What it does: Compromises cloud-hosted data by either encrypting files directly in the cloud or syncing encrypted local files with cloud backups.
- Goal: To exploit the widespread adoption of cloud services and increase the attack’s impact.
- Example Tactics:
- Attacking cloud platforms through stolen credentials or vulnerabilities.
12. Hybrid Ransomware
- What it does: Combines multiple tactics, such as locking systems and encrypting files, while also threatening data leakage.
- Goal: To maximize pressure on victims by using multiple attack vectors.
- Example Variants:
- Ryuk: Often used in targeted attacks on high-profile organizations.
Conclusion
Ransomware attacks can cripple businesses, but professional server ransomware data recovery services in Glasgow provide the expertise needed to recover data, minimise downtime, and safeguard systems against future attacks. By working with our experienced recovery specialists, businesses can navigate ransomware incidents effectively and restore normal operations with confidence.